The EU Cyber Resilience Act (“CRA”) establishes mandatory cybersecurity requirements for most hardware and software products made available on the EU market. While the CRA's date of full application (11 December 2027) is still ahead, 2026 is the year in which first obligations take effect and key operational infrastructure becomes available. In particular, the manufacturers' obligations to notify actively exploited vulnerabilities and severe incidents will start to apply, the notified-body framework for conformity assessment will become operational, and the first standards are expected to be finalized. This article provides an overview of the recent developments and upcoming key milestones for CRA compliance that manufacturers and other economic operators should consider in their compliance projects to avoid last-minute bottlenecks.
Background
The CRA (Regulation (EU) 2024/2847) introduces essential cybersecurity requirements on the planning, design, development, and maintenance of “products with digital elements” and includes obligations that economic operators like manufacturers, importers and distributors must satisfy when distributing such products in the EU (see our previous blogpost and Digital Transformation Academy video, for a full overview of the CRA).
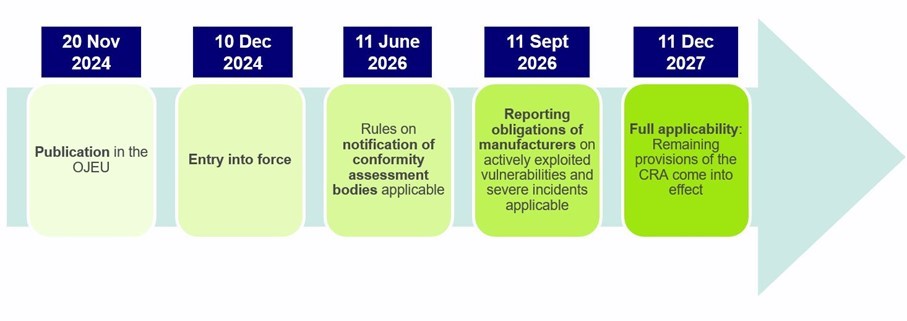
The CRA entered into force on 10 December 2024 and will apply in full from 11 December 2027. However, two key building blocks apply earlier: Obligations for the reporting of exploited vulnerability and severe incidents will apply from 11 September 2026, which is particularly important for all in-scope products that are already placed on the EU market before 11 December 2027. Also, the legal framework on the notification of conformity assessment bodies already applies from 11 June 2026.
Recent Developments
Since late 2025, the Commission has started publishing practical implementation materials and has adopted the first CRA implementing and delegated acts. Read together, these instruments provide further clarification on how the CRA will be operationalized in practice:
- Commission CRA FAQ: In December 2025, the Commission published a CRA implementation Q&A, which is intended to serve as working document. The Q&A provides a first helpful, structured reference point to get an understanding of the CRA in the context of the broader “New Legislative Framework” of EU product rules and the relevant “Blue Guide” guidance of the European Commission. However, it does not yet offer much additional clarity on more challenging edge cases that many manufacturers are currently grappling with.
- Implementing Regulation on the technical description of the categories of important and critical products with digital elements: For the selection of an appropriate conformity assessment method to confirm CRA conformity of a product, manufacturers must determine on basis of the “core functionality” of a product whether it classifies as an important product (Class I or II) or a critical product under Annex III and IV CRA. On 28 November 2025, the Commission adopted Implementing Regulation (EU) 2025/2392 that describes the core functionality of the important and critical product categories and includes some non-exhaustive examples for illustration. It is therefore a key document for companies to consider when applying the “core functionality” test to their products.
- Delegated Act on delaying dissemination of notifications: The Commission also adopted a Delegated Act to specify the terms and conditions under which a computer security incident response team (“CSIRT”) may delay the dissemination of notifications on cybersecurity-related grounds. The CRA requires manufacturers to report actively exploited vulnerabilities and severe incidents via a Single Reporting Platform to be established under the CRA. Notifications go to the competent CSIRT at the manufacturer’s main establishment and are shared with the European Union Agency for Cybersecurity (“ENISA”) and other relevant EU CSIRTs, unless dissemination is delayed on justified cybersecurity grounds under the Commission’s Delegated Act. The Delegated Act will enter into force if neither the European Parliament nor the Council objects within a two-month objection period.
- Draft standards: Further, several draft standards which are currently being developed by the European Standardization Organizations (ESOs) ETSI, CEN, and CENELEC on basis of the Commission’s standardization request (see Implementing decision C(2025)618) moved into the “mature draft” stage, including vertical (product-specific) CRA standards for browsers, password managers, antivirus software, VPNs, network management systems, security information and event management (SIEM), and boot managers. Practically, these drafts can be used as first orientation for engineering decisions for CRA purposes.
What to expect in 2026
2026 can be considered as the “operational readiness” year. While the CRA’s core product requirements apply from 11 December 2027, the framework on notified bodies for conformity assessments and obligations on the reporting of vulnerabilities and severe cybersecurity incidents under the CRA will already start to apply in 2026. The following key developments are most relevant in the coming months:
- Q1/2026 – CRA guidance by the Commission: The European Commission announced that it will publish first guidance for CRA implementation in early 2026. Such guidance may address key issues such as the CRA’s scope with a particular focus remote data processing solutions and free and open-source software (which are new legal concepts introduced by the CRA), the application of support periods in relation to particular categories of products with digital elements, overlap with other EU harmonization legislation and the concept of “substantial modification” for products that are already placed on the EU market (see Art. 26 CRA).
- 11 June 2026 – Framework on notification of conformity assessment bodies starts to apply: Further, the rules for the notification of conformity assessment bodies under the CRA will start to apply from 11 June 2026 (see Chapter IV, Art. 71(2) CRA). Before they can operate as “notified bodies” that are entitled to perform conformity assessments under the CRA, the bodies have to be notified by the notifying authorities for the EU Member State where they are established. This matters for manufacturers that will require third-party involvement under the CRA conformity assessment modules, especially for products in the important and critical category, rather than pure self-assessment.
- 11 September 2026 – Manufacturer reporting obligations start to apply: From this date, manufacturers must report (i) actively exploited vulnerabilities and (ii) severe incidents having an impact on the security of the product with digital elements, via the single reporting platform, which will be established and managed by ENISA. These reporting obligations are operationally demanding, as they come with very short statutory deadlines, including an early warning within 24 hours, notification within 72 hours, and follow-up reporting with final reports no later than 14 days after a corrective measure is available for actively exploited vulnerabilities and within a month for severe incidents. Importantly, these reporting obligations apply to all products in scope of the CRA that are already placed on the EU market, i.e. also legacy products placed on the market before 11 December 2027.
- Q3 2026 – First finalized harmonized standards are available: In line with the timeline of the ESO’s working programme for the CRA, the Commission expects first standardization deliverables to be finalized in Q3 2026. After citation in the EU Official Journal, such standards (at least product-specific vertical standards) can be used by manufacturers for CRA conformity assessments in order to benefit from a presumption of conformity once the CRA is fully applicable.
- 11 December 2026 – First notified bodies are operational: As envisioned under the CRA, a sufficient number of notified bodies should be designated in the EU Member States by 11 December 2026 to ensure sufficient capacities and to avoid bottlenecks (see Art. 35 CRA). In practice, this requires completion of the notification procedures for conformity assessment bodies well before 11 December 2026. Once a conformity assessment body has been successfully notified, it will be added to the “NANDO” notified bodies list (see here for the CRA). Manufacturers that are required to rely on third-party conformity assessments for CRA compliance should monitor the developments in this regard closely.
Getting Ready for CRA Compliance
As a product law, the CRA requires to consider the full lifecycle of products. For most companies, a key objective for 2026 would be to build the minimum operational capability to comply with reporting obligations on day one, while simultaneously laying the groundwork to achieve full CRA compliance by December 2027. Thereby, the following action items could make the difference between a controlled compliance preparation and an end-of-2027 fire drill:
- Scoping and product classification: Perform a CRA applicability assessment and create inventories of in-scope products with digital elements (including essential remote processing), classify products as default, important or critical on basis of their core functionality, and confirm the economic operator roles of entities involved in the distribution of these products. See here for a step-by-step guide for assessing the CRA’s applicability to your products
- Gap analysis: If not done so already, complete a CRA compliance gap analysis to identify any compliance gaps for in-scope products. Issues that will typically need to be addressed include e.g. implementation of support periods in line with CRA standards, vulnerability handling and CRA documentation (see here for a practical walkthrough of the essential documentation requirements).
- Conformity assessment and harmonized standards: Decide on paths for conformity assessments, including self-assessment vs. third-party assessment, as well as use of harmonized standards (key benefit: presumption of conformity) vs. own assessment of compliance with essential cybersecurity requirements. Track relevant key drafts for harmonized standards. If, based on the product classification, notified-body involvement is likely, track the progress in the notification of conformity assessment and monitor NANDO listings.
- Vulnerability and incident reporting: Update existing incident reporting processes by defining triggers and procedures for the handling for “actively exploited vulnerabilities” and “severe incidents” for in-scope products as of 11 September 2026, and implement workflows and reporting templates to meet the staged CRA reporting deadlines.
- Supply chain management: Update supplier contracts to reflect CRA obligations, and include CRA compliance in supplier due diligence procedures. Suppliers of critical components that may impact the ability for CRA compliance by 11 December 2027 should be prioritized.
Authored by Henrik Hanssen.

 Search
Search


 Search
Search

